Integration Guide for Cisco Remote Access with GreenRADIUS 2FA
Before starting, make sure GreenRADIUS is configured with users imported from your LDAP and can communicate with your Cisco ASA
Configuring GreenRADIUS for Cisco ASA
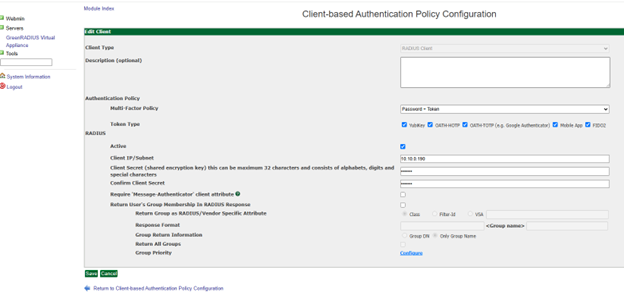
In the GreenRADIUS web admin interface, add the Cisco ASA as a RADIUS client.
- Click the Global Configuration tab
- Click the Client-based Authentication Policies icon
- Enter the IP address of the Cisco ASA. Then enter the same RADIUS secret twice. Then click the Add button.
Configuring the Cisco ASA
Add GreenRADIUS as a RADIUS Server
Before starting, ensure that network interfaces and client profiles are configured correctly.
- Log in to the Cisco ASDM for ASA.
- Open the "Configuration" tab and select "Remote Access VPN."
- Locate "AAA/Local Users" and select "AAA Server Groups." Click the top right Add button to create a new "GreenRADIUS" RADIUS server group:
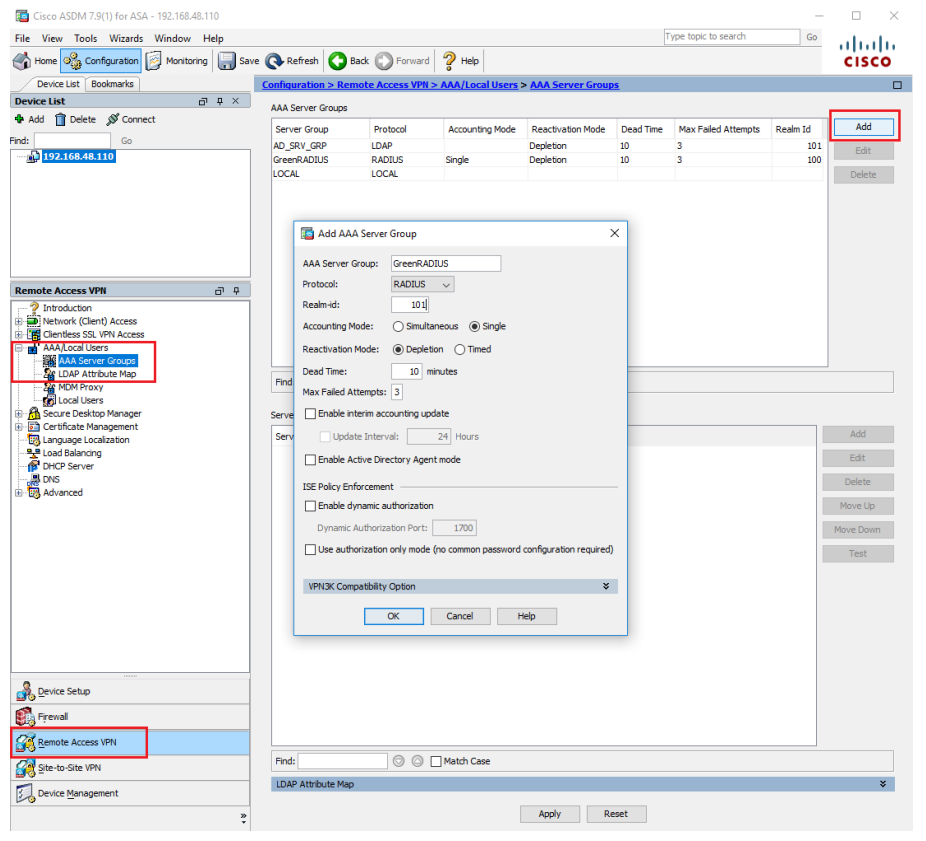
- Select the new "GreenRADIUS" AAA Server Group and click the bottom right Add button. This will open the AAA Server window:
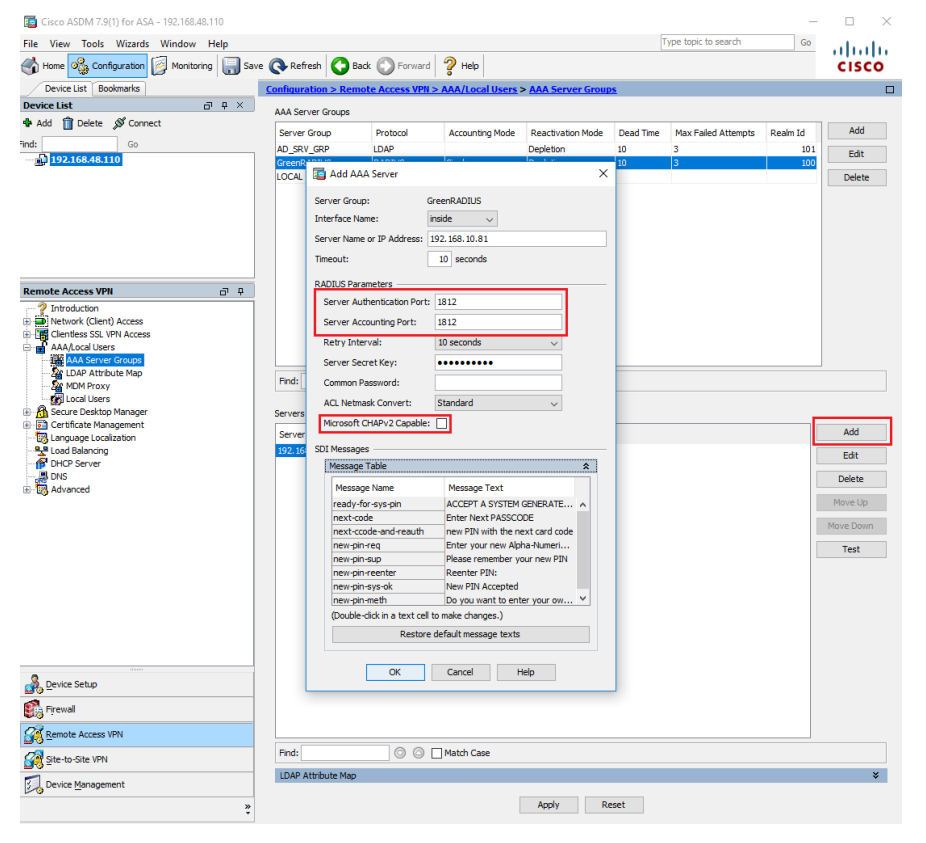
- Server Name or IP Address: greenradius_ip_or_fqdn
- Server Authentication Port: 1812
- Server Accounting Port: 1812
- Server Secret Key: Client Secret provided in the RADIUS Clients tab on the GreenRADIUS web admin interface.
- Microsoft CHAPv2 Capable: Unchecked
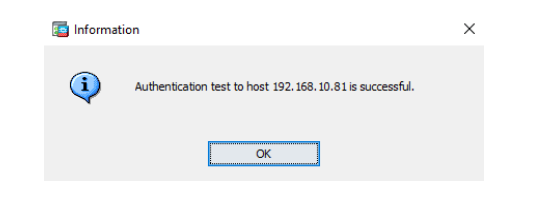
- Click OK. Choose "Test" to verify the above configuration:
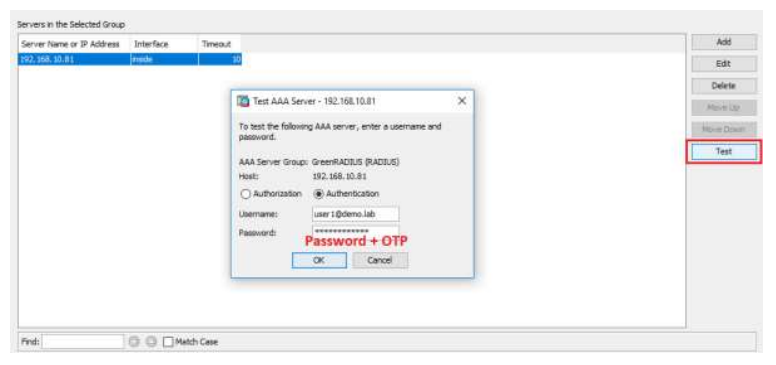
- Select "Authentication." Enter the test user's username and password and append the token's OTP to the password in the Password field, then press "OK."
Cisco Network Client Access Configuration
- Locate "Network (Client) Access" on Remote Access VPN and select your "Connection Profile."
- Under Authentication, choose Method: AAA and AAA Server Group: GreenRADIUS, then "OK."

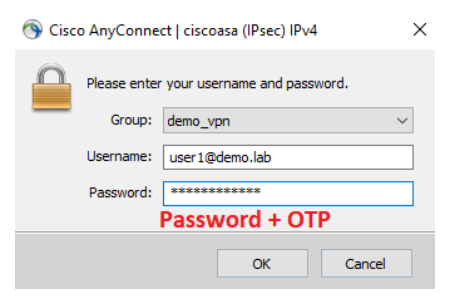
- We have successfully configured your Cisco ASA Remote Access VPN with GreenRADIUS. Now, just connect from a client machine by appending the token's OTP to the password.
Updated 2025-10-30
© 2026 Green Rocket Security Inc. All rights reserved.
© 2026 Green Rocket Security Inc. All rights reserved.