2FA for Windows Logon
GreenRADIUS can enforce two-factor authentication for Windows Logon. Our Windows Logon solution works with:
- Windows PCs (Windows 10 and 11)
- Windows Servers (2016, 2019, 2022, and 2025)
- domain-joined
- non-domain-joined
- desktop/physical logon
- RDP logon
- online logons
- offline logons
During configuration, make sure GreenRADIUS is reachable from your Windows machines over ports 443 and 9443. Also, make sure GreenRADIUS has an active license that enables our U2F Module. (You can check this in the GreenRADIUS web admin interface on the License tab.)
Also, if you are adding 2FA to domain-joined Windows machines, make sure GreenRADIUS has a domain whose name matches exactly with the name of the domain that the Windows machines are joined to.
On each Windows machine, a small Green Rocket Security Windows agent will need to be installed when logged in as an administrator. (Contact us for our latest Windows agents.)
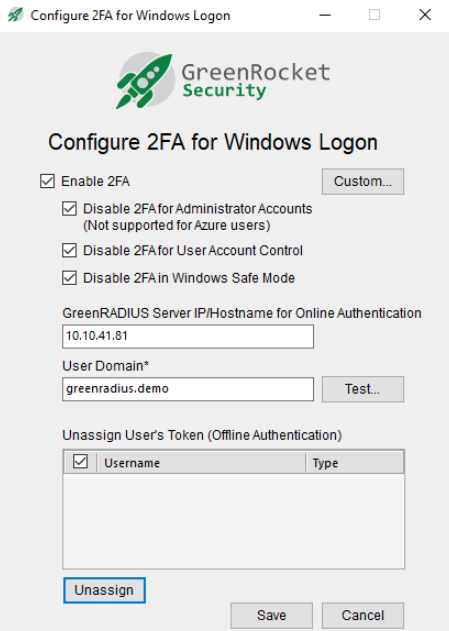
- Enable 2FA: This should be checked to enforce 2FA with GreenRADIUS. If unchecked, 2FA will not be enforced.
- Disable 2FA for Administrator Accounts: If checked, all administrator accounts will bypass 2FA and will only need passwords to log in.
- NOTE: If an offline login is attempted for a domain account, the login will always require 2FA, even if this checkbox is checked and the user is a domain administrator.
- Disable 2FA for User Account Control: If checked, User Account Control (UAC) logins will bypass 2FA and will only need passwords to log in.
- Disable 2FA in Windows Safe Mode: If checked, when Windows is booted in Safe Mode, 2FA will be disabled. (NOTE: In Safe Mode, the agent cannot be uninstalled, but the "Enable 2FA" checkbox can be unchecked.)
- GreenRADIUS Server IP/Hostname for Online Authentication: Enter the IP address or hostname of GreenRADIUS. (The "https://" and ":9443/" will automatically be inserted.)
- User Domain: Enter the GreenRADIUS domain where LDAP users have been imported. (Only one GreenRADIUS domain can be configured.)
After the above has been configured, click the Test button. You should see a successful message appear. If not, double check the GreenRADIUS IP address/hostname and the GreenRADIUS domain, and then try the Test button again.
The Custom... button will allow for more granular 2FA policies on the Windows machine. These policies will override policies in GreenRADIUS. (For example, if user1 has 2FA enforced in GreenRADIUS, but in the Custom... button, user1 is configured to bypass 2FA, user1 will only need a password to log in.)
After configuration, save the settings. You may be asked to restart in order for changes to take effect.
Online Authentication Attempts (GreenRADIUS is reachable)
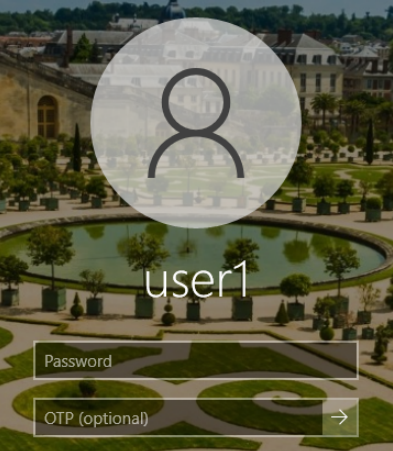
After entering the username and password, users may use the following tokens for online authentication attempts:
- YubiKey OTP: Insert the YubiKey in a USB port, and with the cursor in the OTP field, touch the YubiKey button.
- YubiKey OATH-HOTP: Insert the YubiKey in a USB port, and with the cursor in the OTP field, touch the YubiKey button.
- FIDO U2F tokens: Insert the FIDO U2F token in a USB port, leave the OTP field blank, and after entering the password, press the Enter key on your keyboard or click the login arrow on the screen. Then touch the FIDO U2F button after it starts to flash. The FIDO U2F token used the first time successfully to log in by the user will automatically be assigned to the user in GreenRADIUS. This auto-provisioning of FIDO U2F tokens is the only way these tokens can be assigned to users.
- Authenticator app: Enter the current OTP from the Authenticator app into the OTP field. Then press Enter.
- Green Rocket 2FA Mobile App: With no token inserted in a USB port, and after entering the password, press Enter. A push notification will be sent to the user's phone to approve or reject the logon attempt. Tap
Approveon the app to log in.
Important Note: For local Windows user accounts, corresponding user accounts with the same usernames as the local user accounts must be present in the LDAP being used with GreenRADIUS. Then, those user accounts will need to be imported into GreenRADIUS. Also important, if tokens using OTPs are going to be used, the LDAP password for these users must be set to Pa$$word@123. This password is not necessary for users using FIDO U2F tokens and the Green Rocket 2FA Mobile App. Local users would still use their local Windows passwords to log in to Windows. (This fixed password will never be used for a Windows login.)
RDP Logon
To log in via RDP, launch the mstsc.exe application. After selecting the IP address or hostname, on the RDP logon screen, enter username and password only.
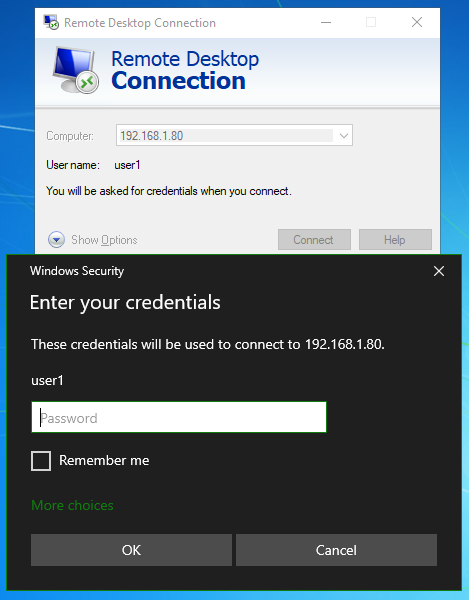
Once that is successful, users will see the Windows Logon screen. The following tokens can be used:
- YubiKey OTP: Insert the YubiKey in a USB port, and with the cursor in the OTP field, touch the YubiKey button.
- YubiKey OATH-HOTP: Insert the YubiKey in a USB port, and with the cursor in the OTP field, touch the YubiKey button.
- Authenticator app: Enter the current OTP from the Authenticator app into the OTP field. Then press Enter.
- Green Rocket 2FA Mobile App: With no token inserted in a USB port, and after entering the password, press Enter. A push notification will be sent to the user's phone to approve or reject the logon attempt. Tap
Approveon the app to log in.
Note: FIDO U2F tokens cannot be used for RDP logon attempts.
Offline Authentication Attempts (GreenRADIUS is not reachable)
Only FIDO U2F tokens can be used when the Windows machine cannot reach GreenRADIUS. The logon experience will be the same when using FIDO U2F tokens, whether the Windows machine is online or offline. Users will insert the FIDO U2F token in a USB port, leave the OTP field blank, and after entering the password, press the Enter key on the keyboard or click the login arrow on the screen. Then touch the FIDO U2F button after it starts to flash.
The FIDO U2F token used to successfully log in the first time in offline mode will automatically be assigned to the user. Offline FIDO U2F tokens are managed on the Windows agent on the PC or Server, not in GreenRADIUS. To unassign an offline FIDO U2F token, open the agent as an administrator, select the user, and click the "Unassign" button.
Token Type By Login
| Token Type | Online Login | Offline Login | RDP |
|---|---|---|---|
| YubiKey OTP | Yes | No | Yes |
| YubiKey OATH | Yes | No | Yes |
| YubiKey FIDO U2F | Yes | Yes | No |
| Authenticator App | Yes | No | Yes |
| Green Rocket 2FA Mobile App | Yes | No | Yes |
Note: ARM64-based Windows devices are not yet supported by our Windows agent
© 2026 Green Rocket Security Inc. All rights reserved.