GreenRADIUS Windows 2FA - GPO Deployment Guide
Prerequisites
You must have the following for the GreenRADIUS two-factor authentication solution for Windows to be deployed properly via GPO.
- GreenRADIUS v4.3.3.3 or later
- Active Directory users imported into GreenRADIUS
- Shared folder on your machine or network containing MSI setups
- Windows 2FA GPO bundle
Pre-deployment configuration file
- Extract the Windows 2FA GPO bundle into a shared folder on your Domain Server:
GreenRADIUS 2FA for Windows Logon.msigrs_settings.reggrs_cleaner.reg
- Right click on
grs_settings.reg. Choose Open With → Notepad and you will see multiple key-value pairs to set in the Windows registry.
Some of the values for the given keys need to be changed depending on your desired configuration. Please see the following list of parameters (keys), what they mean, and when you should modify (or not) the values corresponding to these keys.
Legend
grsAddress
This points to your GreenRADIUS server, and it can be an IP address or hostname.grsDomain
This points to your target domain in GreenRADIUS.grsErrorLevel
This is used to set the verbosity level of logging, and the default value is dword:00000004. It is advised to leave it as is.enabled
This is the flag that decides whether Windows two-factor authentication (Win2FA) must be enabled or not on your machine. Set it to dword:00000001 to enable Windows two-factor authentication on your machine.byPassAdministrators
This is the flag that decides if Windows 2FA should be enabled for users that fall under the Administrator role. If enabled, administrative accounts won’t be prompted for two-factor authentication. It is set by default and we recommend to leave it as is.safemodeEnabled
This is the flag that decides if two-factor authentication should happen when a user boots into safe mode on a Windows machine. By default it is set to (0) and we recommend to leave it as is.safemodeBypassAdmin
This is the flag that decides if an Administrative account will be prompted for a two-factor authentication on a Windows machine. By default it is set and we recommend to leave it as is.
Group Policy Objects
GreenRADIUS 2FA settings and custom preferences
If custom settings will be configured (such as custom policies for particular AD groups or users), a GPO can be used for these custom settings.
Create a GPO for grs_settings.reg:
-
In your Domain Server, open Server Manager, click Tools, and open Group Policy Management.
-
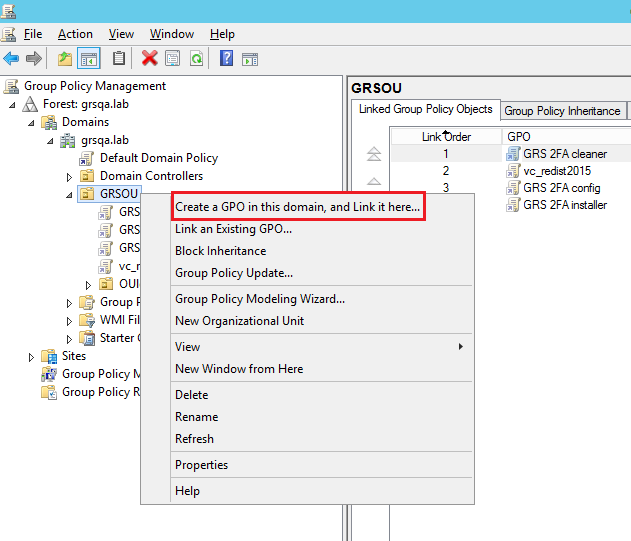
Right click the target Domain/OU/Group and click “Create a GPO in this domain, and link it here...”
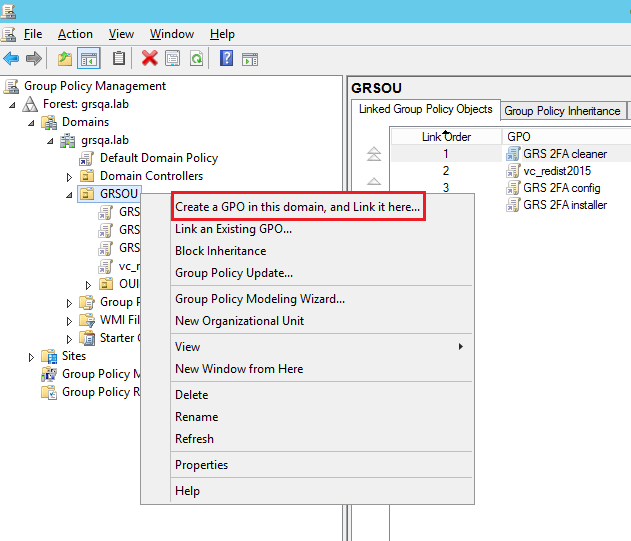
- In the New GPO window, type any name for this new policy e.g. “GRS 2FA config” and then click OK.
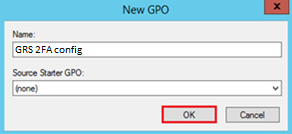
- On the Group Policy Management console, right click the new “GRS 2FA config” GPO and click Edit.
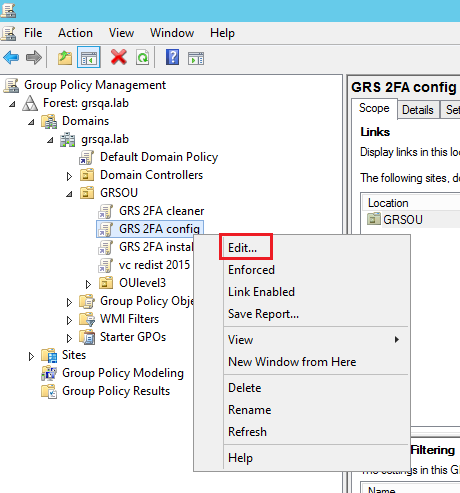
-
In the Group Policy Management Editor, under Computer Configuration, expand Policies, and then expand Windows Settings.
-
Choose Scripts (Startup/Shutdown) and click Startup.
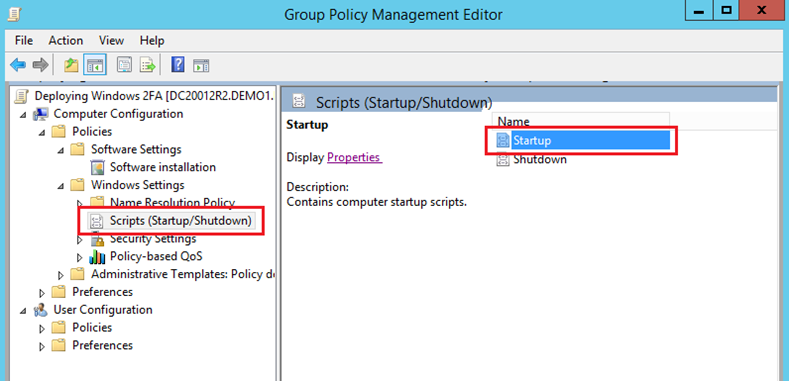
- Click on Show Files and copy/paste “grs_settings.reg” from your shared folder.
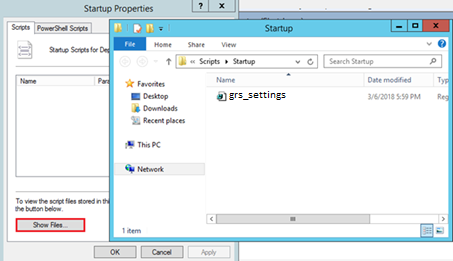
- In the Startup Properties window, click on Add and apply the following:
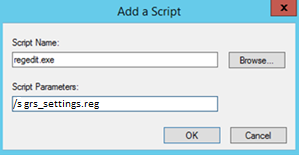
- Script Name:
regedit.exe - Script Parameters:
/s grs_settings.reg
- Script Name:
-
Click OK.
-
In the Startup Properties window, click OK and close this Group Policy Management Editor.
GreenRADIUS 2FA installer
Create a GPO for software installation:
-
In your Domain Server, open Server Manager, click Tools, and open Group Policy Management.
-
Right click the target Domain/OU/Group and click “Create a GPO in this domain, and link it here…”
- In the New GPO window, type any name for this new policy e.g. “GRS 2FA installer 64bit” and then click OK.
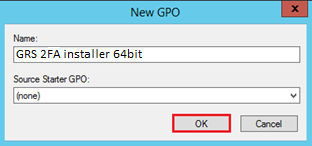
- On the Group Policy Management console, right click the new “GRS 2FA installer 64bit” GPO and click Edit.
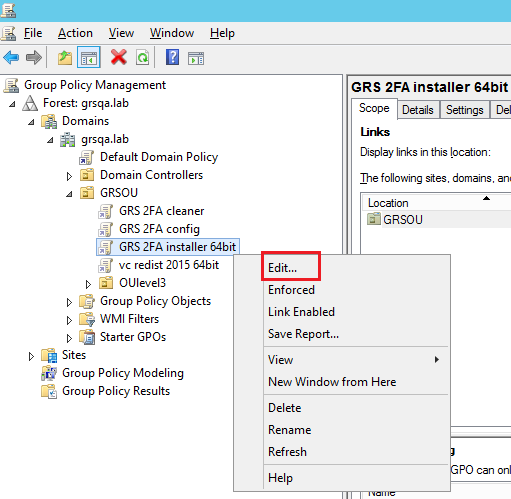
-
In the Group Policy Management Editor, under Computer Configuration, expand Policies, and then expand Software Settings.
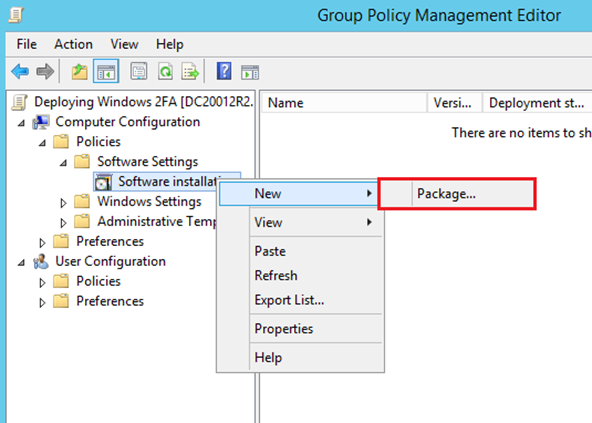
-
Right click Software installation. From the context menu, click New, and then click Package.
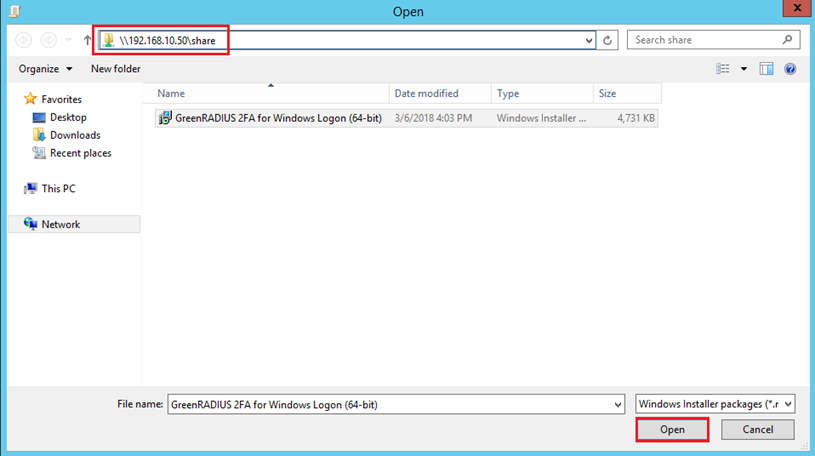
- In the Open dialog box, browse to
\your_server_ip\shared_folder, click on “GreenRADIUS 2FA for Windows Logon.msi”, and then click Open.
-
On Select deployment method, select Assigned.
-
Click OK to complete the setup.
-
Wait for a few seconds and verify that GreenRADIUS 2FA for Windows Logon is listed in the Group Policy Management Editor.
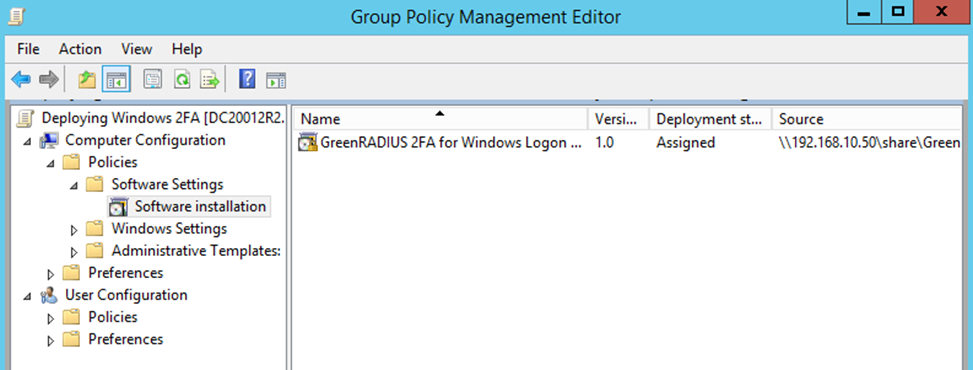
- Close this Group Policy Management Editor
Group Policy Link Order
Click on your target Domain/OU/Group, the GPOs should reflect the following link order:
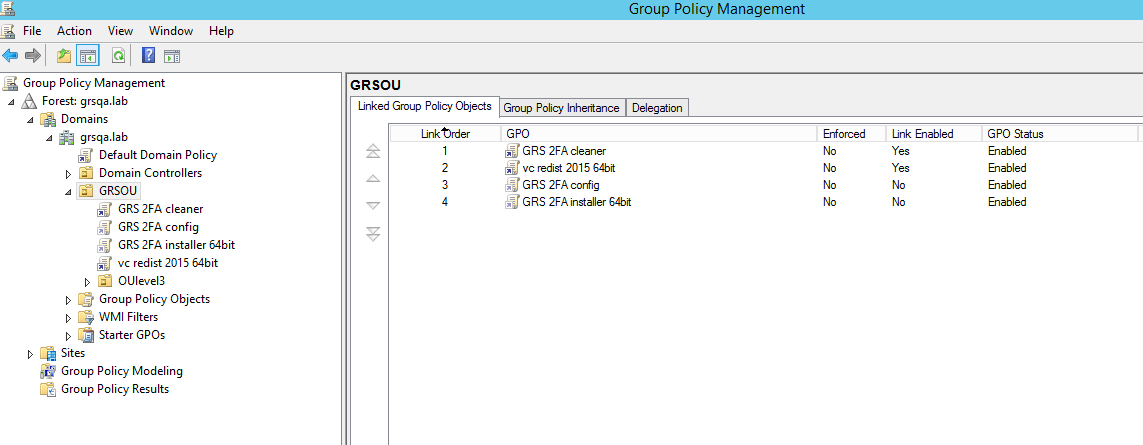
- GRS 2FA cleaner (optional – needed when updating from 1.0.8 or below)
- GRS Offline token unassignment (optional)
- GRS 2FA config
- GRS 2FA installer 64bit
The installer looks for the GRS 2FA config provided, however a system reboot is required to fully enable GreenRADIUS 2FA for Windows.
GRS Offline Token Unassignment
GreenRADIUS offline U2F token assignments can unassigned via GPO. (This can be done per user to multiple machines.) Create a GPO for offline U2F token unassignment.
-
On your Domain Controller, open Server Manager, click Tools, and open Group Policy Management.
-
Right click the target Domain/OU/Group and click “Create a GPO in this domain, and link it here…”
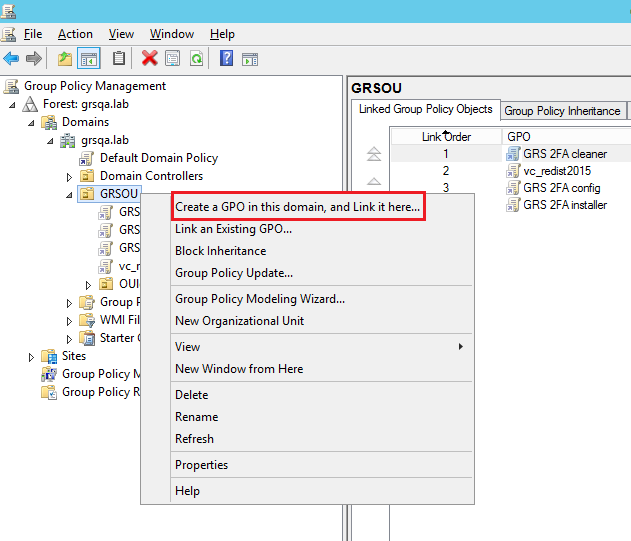
- On the Group Policy Management console, right click the newly created GPO and click Edit.
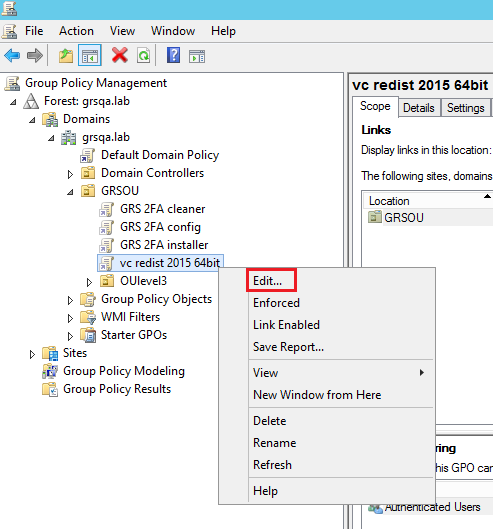
-
In the Group Policy Management Editor, under Computer Configuration, expand Preferences, and expand Windows Settings then Registry.
-
Add new entry, Action should be Delete then specify key path accordingly.
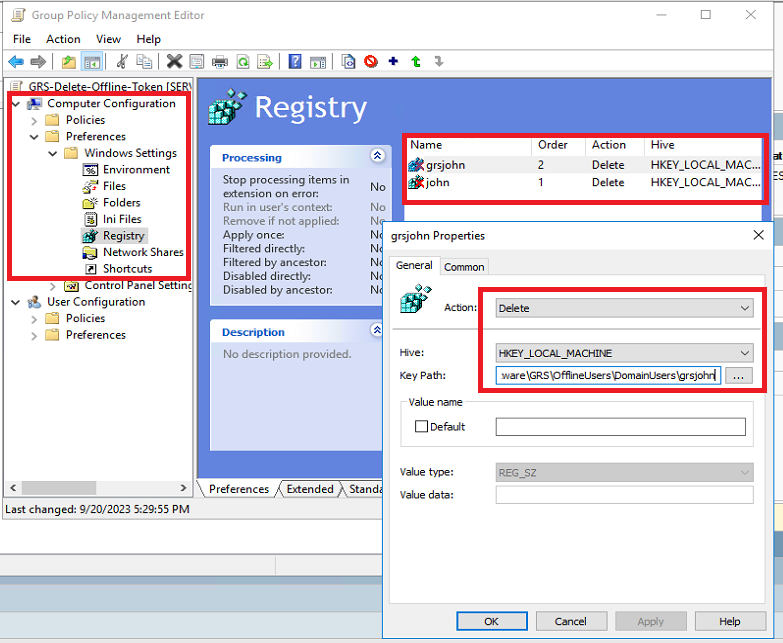
For Domain Users:
KeyPath: SYSTEM\CurrentControlSet\Software\GRS\OfflineUsers\DomainUsers\username
For Local Users:
KeyPath: SYSTEM\CurrentControlSet\Software\GRS\OfflineUsers\LocalUsers\username
© 2026 Green Rocket Security Inc. All rights reserved.