Configuring Our GRS PAM Module for 2FA for RedHat, CentOS, or Ubuntu
Introduction
GreenRADIUS can be used to enforce two-factor authentication for access to RedHat, CentOS or Ubuntu machines. One way to do this is with our custom GRS PAM Module. Our GRS PAM Module uses HTTPS communication instead of RADIUS, avoiding the need to manage each machine as a RADIUS client.
The following login methods can be protected with the GRS PAM Module:
- SSH
- console
sudo- GNOME
Contact us today to evaluate GreenRADIUS with our custom GRS PAM Module.
Prerequisites
- GreenRADIUS with users imported and reachable from the client machine running RedHat 7, 8, or 9 or Ubuntu 20, 22, or 24
- Users imported into GreenRADIUS from your LDAP must have matching usernames with local user accounts on the Linux machine
- GRS PAM Module from Green Rocket Security (at least v2.7.1).
- If SELinux is installed on the client machine (it is usually installed by default on RedHat), then you will need to do one of the following:
- Set SELinux to disabled or permissive mode. You can change this setting in the
/etc/selinux/configfile. After editing the file, reboot your system for the changes to take effect. - After you have unpacked the files from the module archive (step 2 below), run
sudo chcon system_u:object_r:lib_t:s0 grs_pam.soin your terminal to set the appropriate security context on the module.
- Set SELinux to disabled or permissive mode. You can change this setting in the
- You will need a version of Python and the corresponding Requests module.
- RedHat:
sudo yum install python3andsudo pip3 install requests - Ubuntu:
sudo apt install python3 python3-requests
- RedHat:
Steps
- Run
sudo su -to enter super user mode - Unpack the provided module archive. You should have three files:
make_request.py,config, andgrs_pam.so. - Run
chmod +x make_request.py - Run
chmod +x grs_pam.so - Run
mkdir /etc/grs-pam - Run
mv make_request.py /etc/grs-pam - Run
mv config /etc/grs-pam - Move the
grs_pam.soto the appropriate location depending on your OS:- RedHat:
/lib64/security - Ubuntu:
/lib/x86_64-linux-gnu/security
- RedHat:
- Edit the /etc/grs-pam/config file to update the following:
- SERVER: the IP address/hostname of the GreenRADIUS instances or a list of IP addresses/hostnames
- e.g.
[SERVER:greenradius]
- e.g.
- VERIFY_SSL: flag to enable/disable peer certificate verification
[VERIFY_SSL:YES]- for enforcing certificate verification[VERIFY_SSL:NO]- for disabling certificate verification
- CERT: the absolute path to a CA_BUNDLE file or directory of trusted CA certs to be used to verify the GreenRADIUS certificate
- e.g.
[CERT:/etc/ssl/certs/ca-bundle.crt] - NOTE: If a directory is specified with CERT, it must have been processed using the c_rehash utility supplied with OpenSSL.
- e.g.
- TIMEOUT: the number of seconds the PAM module will wait for GreenRADIUS to respond
- e.g.
[TIMEOUT:10]
- e.g.
- SERVER: the IP address/hostname of the GreenRADIUS instances or a list of IP addresses/hostnames
- Edit the
sshdconfiguration to setChallengeResponseAuthenticationandKbdInteractiveAuthenticationtoyeswherever they occur. The default configuration file is found in/etc/ssh/sshd_config, but there may beIncludecommands in this file which link it to other files, so those will need to be searched as well. Note thatChallengeResponseAuthenticationorKbdInteractiveAuthenticationmay occur multiple times across those files, or even in the same file; be sure to set all occurrences toyes. - Run
service sshd restart.
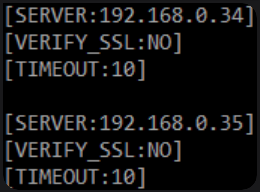
It is possible to configure multiple GreenRADIUS servers by using a set of SERVER directives. Timeout and certificate settings must be configured separately for each server with the appropriate TIMEOUT, VERIFY_SSL, and CERT directives. In this configuration, the PAM module will attempt to contact each server in turn. If one server fails to respond, the next is tried. This is useful for high availability configurations.
- Edit one of the following files depending on which login method(s) you want to protect:
- SSH:
/etc/pam.d/sshd - console:
/etc/pam.d/login sudo:/etc/pam.d/sudo- GNOME:
/etc/pam.d/gdm-password - GNOME Screen Lock:
/etc/pam.d/gnome-screensaver
- SSH:
- Add this line at the top of the file:
auth required grs_pam.so. - If you would like password and OTP to be prompted for separately, add the word
separate_otp_promptto the end of the previous line:auth required grs_pam.so separate_otp_prompt. Note that this will not work for all authentication methods, as not all permit custom prompts. - Add a
#in front of the following line to comment it out:- RedHat:
auth substack password-auth - Ubuntu:
@include common-auth
- RedHat:
- Try a test login attempt with a user. In the password field, enter Password+OTP (append OTP to the end of the password), then hit Enter.
If you have any questions during your evaluation or configuration, please do not hesitate to contact us!
Note for advanced users
For advanced users designing more complex PAM authentication flows, note that
the GRS PAM HTTPS Module only returns PAM_SUCCESS or PAM_FAIL, never any other code.
This behavior will not change in future updates unless gated behind a command-line option.
© 2026 Green Rocket Security Inc. All rights reserved.